The official website of Embassy of Kazakhstan in Delhi having SQL injection Vulnerability, and Hacker with codename - Abs0luti0n has successfully Extract the database tables info and leak it on a pastebin note including Admin's Username and Password.
Tuesday, January 31, 2012
Monday, January 30, 2012
FBI will Monitor Social Media using Crawl Application
The Federal Bureau of Investigation is looking for a better way to spy on Facebook and Twitter users. The Bureau is asking companies to build software that can effectively scan social media online for significant words, phrases and behavior so that agents can respond.A paper posted on the FBI website asks for companies to build programs that will map sentiment and wrongdoing.
“The application must be infinitely flexible and have the ability to adapt quickly to changing threats to maintain the strategic and tactical advantage,” the Request for Information said, “The purpose of this effort is to meet the outlined objectives…for the enhancement [of] FBI SOIC’s overall situation awareness and improved strategic decision making.”The tool would be used in reconnaissance and surveillance missions, National Special Security Events (NSS) planning, NSSE operations, SOIC operations, counter intelligence, terrorism, and more.
Although the police, including in Britain, already use Facebook routinely to ascertain the whereabouts of criminals, automatically filtering out irrelevant information remains challenging. The new FBI application will be able to automatically highlight the most relevant information. The FBI is seeking responses by 10 February.
Universal Music Portugal database dumped by Hackers
Another Latest Tip come in my Inbox today about the leak of Database of Universal Music Portugal's website. Hacker did not mention his name,or Codename, But he enumerate the Database and Extract it by Hacking the Site.
100's of Tables from Database and Users Data has been leaked via a pastebin File. It includes the Usernames, Passwords and Emails ID's of Users of Site.
Immediate after the Hack, The Universal Group taken down the site for maintenance.
100's of Tables from Database and Users Data has been leaked via a pastebin File. It includes the Usernames, Passwords and Emails ID's of Users of Site.
Immediate after the Hack, The Universal Group taken down the site for maintenance.
Sunday, January 29, 2012
Zulu - Zscaler Malware Scanning Service
Zscaler has launched a new free online service called Zulu that can assess the security risk associated with URLs by analyzing the content they point to, as well as the reputation of their corresponding domain names and IP addresses.
Zulu allows security savvy users who investigate various web attacks to choose what User-Agent and Referrer headers the scanner will use when accessing a URL. "A unique benefit of this approach is that we can deliver a risk score even when the page content is no longer available," said Michael Sutton, vice president of security research at Zscaler. "While we can't access the page, we can still assess the URL and host and when they deliver a high risk score despite a lack of page content, one can often conclude the page was indeed malicious but has since been taken down," he explained.
Depending on the type of content a URL points to, Zulu can perform an antivirus scan using the VirusTotal multi-engine service, try to match a file's MD5 hash in Zscaler's database, search for known JavaScript obfuscation patterns and phishing heuristics, or use the company's malware detection technologies.
Zulu allows security savvy users who investigate various web attacks to choose what User-Agent and Referrer headers the scanner will use when accessing a URL. "A unique benefit of this approach is that we can deliver a risk score even when the page content is no longer available," said Michael Sutton, vice president of security research at Zscaler. "While we can't access the page, we can still assess the URL and host and when they deliver a high risk score despite a lack of page content, one can often conclude the page was indeed malicious but has since been taken down," he explained.
Depending on the type of content a URL points to, Zulu can perform an antivirus scan using the VirusTotal multi-engine service, try to match a file's MD5 hash in Zscaler's database, search for known JavaScript obfuscation patterns and phishing heuristics, or use the company's malware detection technologies.
Saturday, January 28, 2012
FBI warning about Banking Trojan “Gameover”
Oh no!!FBI is warning of a banking trojan called "Gameover".No it doesn't have to do with video games, but it does have to do with the security of your bank!
Organized crooks have begun launching cyber attacks against banks and their customers as part of a smoke screen to prevent victims from noticing simultaneous high-dollar cyber heists. On Friday the FBI issued a warning about a banking trojan named Gameover. It’s a new variant of Zeus, a user credential stealing malware that targets online bank users. Zeus has been around for years, and every now and then a new version with a new twist pops up.
Gameover has also been implicated in Distributed-Denial-of-Service attacks that temporarily-disable bank websites to draw attention away from fraudulent transactions. Like another Zeus variant, Troj/BredoZp-GY, Gameover uses e-mail spam to propagate, and the safest way to keep Gameover away from your PC is to avoid links and file attachments that are contained in unfamiliar e-mail messages.
Interview With The Saudi Hacker Who Hacked and Leaked Million Israeli Credit Cards
Why would someone hack into a website and steal million credit cards and later leaks the credit card numbers without even using them? What was the intention, what was the goal? The Saudi hacker made his political point by doing what is known as biggest credit card hack in the history of hacking. We got a chance to talk with this 19-year-old Saudi hacker on skype. He calls himself ”0xOmar”.
Friday, January 27, 2012
US Top Government Security Website Hacked by Anonymous and Login Details Leaked
US Federal Trade Commission (FTC) website has been hacked and taken down by Anonymous hackers against MegaUpload crackdown. FTC website provides Internet security solution and advice to its consumers. Hacktivists not only left their ” We are Legion” message but also gained access to back-end MySQL database and ended up with leaking complete list of login details, consisting of password hashes on http://pastebin.com/mJWUDtGD. At the time I was writing this article, http://onguardonline.gov/ was down.
French President’s Website Hacked by Anonymous Hackers
Anonymous hackers have attacked again, this time the French president’s website has been hacked and taken down against the French support for Megaupload crackdown and for officially supporting the SOPA and PIPA legislation, this Friday. Anonymous left their official ”We are legion” message on the Presidential website. According to RT
Thursday, January 26, 2012
Hannibal Hacker, Exposes Another 1 Million Facebook Member Login Credentials – Claims The List Belongs to Arab World
Hannibal Hacker, who is known for leaking over 30,000 Facebook & Email Accounts two weeks ago, has hit back with another hack of 1 Million Facebook Member Login Credentials that according to him belongs to Middle East and Arabs across the globe.
Hannibal Hacker has posted a huge list of download links for over 1 million facebook and email passwords, which is available on PasteBin.
According to the hacker:
Anonymous Hacker’s Message to Congress on SOPA
Anonymous hackers had sent a message to congress on SOPA and PIPA legislation, though the message was sent in the end of 2011 but its effectiveness can be witnessed now, when Anonymous has done what they mentioned in their message to congress by taking down US and French government websites.
Wednesday, January 25, 2012
Microsoft launching Real Time Hosted Threat Intelligence Feed
Microsoft is to offer a real-time intelligence feed of botnet and e-crime data to public and private sector subscribers, according to security company Kaspersky. Currently, Microsoft is testing a real-time feed to distribute information collected from several sources on major botnets, including Rustock, Waldec and Kelihos networks.
Tuesday, January 24, 2012
Arab Facebook logins posted by Israeli hacker
In four separate posting on Saturday to the Pastebin website, an Israeil hacker calling himself Hannibal announced he had published emails and logins of 100,000 allegedly Arab Facebook users. He also made the data available on 14 other file-sharing sites.
According to a published report by an investigator who downloaded the data from the file-sharing sites, the number of stolen Facebook accounts is likely closer to 20,000.
URL redirection Vulnerability in Google & Facebook
An open redirect is a vulnerability that exists when a script allows redirectionto an external site by directly calling a specific URL in an unfiltered,unmanaged fashion, which could be used to redirect victims to unintended,malicious web sites. A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect.
A similar vulnerability is reported in Google by "Ucha Gobejishvili ( longrifle0x )". This problem may assist an attacker to conduct phishing attacks, trojan distribution, spammers.
Url: https://accounts.google.com/o/oauth2/auth?redirect_uri=http://www.something.com
Same vulnerability in Facebook, Discovered by ZeRtOx from Devitel group:
http://www.facebook.com/l.php?h=5AQH8ROsPAQEOTSTw7sgoW1LhviRUBr6iFCcj4C8YmUcC8A&u=www.something.com
Impact of Vulnerability :
- The user may be redirected to an untrusted page that contains malware which may then compromise the user's machine. This will expose the user to extensive risk and the user's interaction with the web server may also be compromised if the malware conducts keylogging or other attacks that steal credentials, personally identifiable information (PII), or other important data.
- The user may be subjected to phishing attacks by being redirected to an untrusted page. The phishing attack may point to an attacker controlled web page that appears to be a trusted web site. The phishers may then steal the user's credentials and then use these credentials to access the legitimate web site.
Monday, January 23, 2012
Anonymous Attack on Brazilian Websites – Tangara da Serra City Website Hacked and Defaced
Anonymous hackers have hacked and defaced three Brazilian websites, One of Brazil’s federal district, second belongs to a famous Brazilian singer and the third one is Tangara da Serra city’s website in protest against the federal raid and shutdown of Megaupload.com.
Anonymous hackers have launched #OpMegaUpload against the American government and any government who supports the shutdown. Last week Anonymous hacked FBI and US Department of Justice website against the shutdown of Megaupload.
#OpMegaUpload – CBS Broadcasting Website Hacked by Anonymous Hackers
Data Stealing Malware on Internal Computer of Japan Space Agency
Japan Aerospace Exploration Agency (JAXA) announce that their computer has been infected with a virus, leading to a possible leak of data on its H-II Transfer Vehicle (HTV) the craft popularly known as Konotori that hauls cargo for the International Space Station (ISS). JAXA still isn't sure how the virus got on the computer, or who put it there.
Sunday, January 22, 2012
Wireless Penetration Testing Series Part 2: Basic concepts of WLANs
Wireless Penetration Testing Series Part 2: Basic concepts of WLANs
This blog post is in continuation of the Wireless Penetration Testing and Hacking series we started (Part 1: Getting Started with Monitoring and Injection) on the basis of the “SecurityTube Wi-Fi Security Expert” (SWSE) course which is based on the popular book “ Backtrack 5 Wireless Penetration Testing”.
In the third video, the instructor talks about some of the basic concepts of WLANs. We learn that communication over WLAN's happens over frames. There are mainly 3 types of WLAN frames which are Management frames, Control frames, and Data frames. These types of packets also have different subtypes . We learn that an SSID is a name given to an Access point or a network consisting of multiple Access points. We then learn about Beacon frames which are broadcast frames sent out periodically by Access point to broadcast their presence in the current RF (Radio frequency) vicinity. The instructor then starts wireshark and analyzes a beacon frame passing through the network. We learn that a beacon frame is of the type Management and of the subtype 0x08 which denotes that it is a beacon frame. We learn that the beacon frame has 2 types of Parameters (Fixed and tagged). The tagged parameters gives us a lot of information about the network, such as the SSID, the current channel at which the AP is residing, the Vendor specific tag and lots of other information. Everything in this frame is in plaintext, hence if an attacker has the capability to inject packets into the network, then he will be able to inject arbitrary beacon frames into the network or even spoof some of the legitimate Access points which may confuse the client. Same is the case for any type of WLAN frame. Hence all the clients in the RF vicinity will recognize this as a new Access point.
The instructor then gives a demo of the tool mdk3 (available by default in backtrack), which he uses to inject various beacon frames with different BSSID's onto different channels in the network. The tool constantly changes your MAC address to do this. The clients recognize this as a legitimate AP and shows it in it's list of available networks.
Saturday, January 21, 2012
Tit for Tat - Anonymous Hackers Brings Down FBI website for #OpMegaupload
Megaupload.com, one of the world's most popular sources of online piracy, has been shut down by a federal indictment issued Thursday, which seized and charged seven people connected with it with running an international enterprise based on internet piracy. Online piracy by the two companies - Megaupload Ltd and Vestor Ltd - generated more than $ 175 million in criminal proceeds and caused more than half a billion dollars in harm to copyright owners
Nigerian Army Education site hacked by Nigerian Hacktivists
Friday, January 20, 2012
More source code stolen, says Symantec
Symantec acknowledged this week that in addition to theft of source code for past versions of some if its security software, its own servers were breached in 2006. Previously, Symantec had claimed the theft of its source code had come only from third-party servers, but the company modified that statement after an internal investigation showed the company's own network was breached.
The latest announcement said that source code for Norton Antivirus Corporate Edition, Norton Internet Security, pcAnywhere, and Norton GoBack had been taken. This is in addition to the Symantec Endpoint Protection 11.0 and Symantec Antivirus 10.2 that the company acknowledged two weeks ago. The two enterprise-class products were more than five years old, the company said. It did not indicate why some of the code was made public six years after the alleged theft took place.
Saudi hacker target Israeli stock exchange and National air carrier
Saudi cyber Hacker OxOmar struck again on Monday. This time disrupted the websites of Israel's stock exchange and National air carrier. Last week he had leaked private information about more than 400,000 Israelis. Credit card companies said around 25,000 numbers, some of them expired, had been posted. The pro-Palestinian group is referring to itself as “Nightmare.”
Thursday, January 19, 2012
DoD ID cards under attack
A pernicious virus that infects the middleware of smart card readers is attacking users of U.S. Department of Defense (DoD) and Windows smart cards. A variant of the Skyipot trojan, the malware uses a zero-day vulnerability in Adobe software to install a keylogger and obtain the PINs and certificate information from smart cards.
The trojan, first identified by Alienvault Labs, appears targeted at a particular type of application.
Cyber War : Another 7000 Israel credit cards Exposed on Internet
This week has began under worse auspices worse for Israel, which, despite its attention to the cyber threats posed by cyber-space, has been victim of a series of attacks that have checkmated the government of Jerusalem.
Kosova Hacker's Security Group of Hackers today claim to release another Another 7000 Israel credit cards on Internet. Last week xOmar from "group-xp" threatened the Israeli people by exposing millions of credit cards. After that Israel said that it will respond to cyber-attacks in the same way it responds to violent terrorist acts, by striking back with force against hackers who threaten the Jewish state.
Hacker will release full Norton Antivirus code on Tuesday
A hacker with code name of 'Yama Tough' announce via Twitter that on Tuesday he will leak the full source code for Symantec Corp's flagship Norton Antivirus software which is 1,7Gb src.
Last week Yama Tough has released fragments of source code from Symantec products along with a cache of emails. The hacker says all the data was taken from Indian government servers. Yama Tough is trying to prove that Indian government was snooping on America and China.
Wednesday, January 18, 2012
Imagine a World Without Free Knowledge : Wikipedia
What exactly is Wikipedia doing?
Wikipedia is protesting against SOPA and PIPA by blacking out the English Wikipedia for 24 hours, beginning at midnight January 18, Eastern Time. Readers who come to English Wikipedia during the blackout will not be able to read the encyclopedia: instead, they will see messages intended to raise awareness about SOPA and PIPA, and encouraging them to share their views with their elected representatives, and via social media.
What are SOPA and PIPA?
SOPA and PIPA represent two bills in the House of Representatives and the Senate respectfully. SOPA is short for the "Stop Online Piracy Act," and PIPA is an acronym for the "Protect IP Act." ("IP" stands for "intellectual property.") In short, these bills are efforts to stop infringement committed by foreign web sites, but, in our opinion, they do so in a way that actually infringes free expression while harming the Internet. Detailed information about these bills can be found here and here. The EFF has summarized why these bills are simply unacceptable in a world that values an open, secure, and free Internet.
Why is this happening?
Nothing like this has ever happened before on the English Wikipedia. Wikipedians have chosen to black out the English Wikipedia for the first time ever, because we are concerned that SOPA and PIPA will severely inhibit people's access to online information. This is not a problem that will solely affect people in the United States: it will affect everyone around the world.
Zappos a division of Amazon got Hacked
A notification mail from Zappos is circulating in Customers that a division of Amazon "Zappos.com" got Hacked by Unknown Hackers. Notification mail indicated that names, email addresses, mailing addresses, and the last four digits of customer's social security numbers have been compromised. Also the databases that contain sensitive billing information, such as credit card numbers, was not accessed by hackers.
According to messages from Zappos CEO Tony Hsieh to employees and customers:
Tuesday, January 17, 2012
400000 Israeli Credit Cards & Information Leaked by Saudi Arabia Hackers
Hacker named "0xOmar" from group-xp, largest Wahhabi hacker group of Saudi Arabia claim to Hack lot of Israeli servers, lot of information about Israeli people including their name, address, city, zipcode, Social Security Numbers (Israeli IDnumbers), mobile phone number, home phone number, credit card number (including exp year, month and CVV). According to announcements from the credit card companies, 6,600 of the stolen cards belong to Isracard Ltd., 4,000 to Leumi Card Ltd., and 3,000 to Israel Credit Cards-Cal Ltd. (ICC-Cal) (Visa).
Hacker says "We daily use these cards to solve our problems, purchasing VPNs, VPSes, softwares, renting GPU clusters, renting cloud servers and much more!". They Claim themselves as part of Anonymous hacking Group from Saudi Arabian. "my goal is reacing 1 million non-duplicate people, which is 1/6 of Israel's population." He said.
Monday, January 16, 2012
Wireless Penetration Testing Series Part 1: Getting Started with Monitoring and Injection
We had promised a while back that we would start a Wireless Security and Penetration testing series based on the SecurityTube Wi-Fi Security Expert (SWSE) course! This course is based on the popular and much appreciated book – “ Backtrack 5 Wireless Penetration Testing”, So here we go .
In the first two videos, the instructor gets us up and running with our lab setup – access points, victim and attacker machines, wireless cards etc. We then learn that there are 2 essential concepts which one needs to be aware of when dealing with security – ability to monitor and ability to actively prevent attacks.
For monitoring, we need to be able to put our wireless cards into “promiscuous mode” so that it can gather all the packets in the air. This is called monitor mode in wireless and we can do this by using a utility called airmon-ng. For active prevention, we need the ability to inject arbitrary packets into the air, this ability is called “packet injection”. In wireless, by using the right drivers and supported cards, we can create and inject custom packets into the air. We will revisit these concepts in later blog posts.
Sunday, January 15, 2012
International Conference on Cyber Security (ICCS) 2012 : Protecting the Cyber World
The FBI is teaming up with Fordham University for the International Conference on Cyber Security. It’s an effort to identify emerging cyber threats and develop ways to mitigate those threats. The ZeuS Trojan has infected almost 4 million computers in the United States alone. Financial losses due to the ZeuS Trojan are estimated at up to $60 million.
The third annual International Conference on Cyber Security: A White Hat Summit (ICCS 2012), a joint effort between the Federal Bureau of Investigation and Fordham University, brings together global leaders from law enforcement, industry and academia at Fordham’s Lincoln Center campus from January 9 through 12, 2012. The conference will include three days of lectures, panel discussions, sponsor presentations, exhibitions, and exceptional networking opportunities.
ICCS 2012, a four-day event features more than 65 unique lectures from keynote, distinguished, plenary and parallel speakers in the disciplines of Emerging Technologies, Operations and Enforcement, and Real Life Experiences. Also included are panel discussions, sponsor presentations, exhibitions and exceptional opportunities to meet and talk with some of the greatest cyber security subject experts in the world.
Register now for ICCS 2012 and receive the standard rate of $695.00. Registrations are handled on a first-come, first-served basis. For more information on confirmed speakers, registration, accommodations, schedules and presentations, we invite you to visit the official ICCS 2012 website at:http://www.iccs.fordham.edu.
The third annual International Conference on Cyber Security: A White Hat Summit (ICCS 2012), a joint effort between the Federal Bureau of Investigation and Fordham University, brings together global leaders from law enforcement, industry and academia at Fordham’s Lincoln Center campus from January 9 through 12, 2012. The conference will include three days of lectures, panel discussions, sponsor presentations, exhibitions, and exceptional networking opportunities.
ICCS 2012, a four-day event features more than 65 unique lectures from keynote, distinguished, plenary and parallel speakers in the disciplines of Emerging Technologies, Operations and Enforcement, and Real Life Experiences. Also included are panel discussions, sponsor presentations, exhibitions and exceptional opportunities to meet and talk with some of the greatest cyber security subject experts in the world.
Register now for ICCS 2012 and receive the standard rate of $695.00. Registrations are handled on a first-come, first-served basis. For more information on confirmed speakers, registration, accommodations, schedules and presentations, we invite you to visit the official ICCS 2012 website at:http://www.iccs.fordham.edu.
Saturday, January 14, 2012
XSS vulnerability reported in Yahoo subdomain website

Vansh Sharma & Vaibhuv Sharma from India Reported another important Cross site scripting XSS vulnerability in Yahoo subdomain as shown.
Vulnerable Link : http://au.tv.yahoo.com/plus7/royal-pains/
Proof of Concept : Search <img src="<img src=search"/onerror=alert("XSS")//"> in box.
Cross-site scripting ( XSS) is a type of computer security vulnerability typically found in Web applications that enables attackers to inject client-side script into Web pages viewed by other users.
Vulnerable Link : http://au.tv.yahoo.com/plus7/royal-pains/
Proof of Concept : Search <img src="<img src=search"/onerror=alert("XSS")//"> in box.
Cross-site scripting ( XSS) is a type of computer security vulnerability typically found in Web applications that enables attackers to inject client-side script into Web pages viewed by other users.
Thursday, January 12, 2012
Finland ISP is blocking the Pirate Bay, Anonymous stand for Freedom of Expression…!
Anonymous has urged its followers to target Finnish anti-piracy body the Copyright Information and Anti-Piracy Centre (CIAPC) after it persuaded the Helsinki District Court to force one of the country's biggest ISPs to block access to The Pirate Bay.
One of the largest internet service providers in Finland, has been forced to block access to The PirateBay for its customers. Elisa issued a press release on the matter moments ago. The decision was given by a local district court in Helsinki. Elisa has stated that they will seek correction to the decision in supreme court.
"The Helsinki District Court ordered the Elisa 26.10.2011 temporarily suspend a penalty of copyright infringing material available to the public via the Pirate Bay," it said in a statement.
Numerous Twitter accounts linked with the Anonymous collective erupted with messages of discontent and - at times - threats of action against the Finnish government. Anonymous at least the Finnish part of it, voiced its disapproval on Twitter. "#SOPA's landed in #Finland today. Blame them", it said in a message sent to Twitter accounts including @AnonymousIRC, @anonymouSabu and @AnonyOps.
"Ladies and gents: today we will focus on Finland. and every country like it who has begun a campaign of censorship. First steps to Cyberwar," tweeted the AnonymouSabu account.
"TANGO DOWN http://www.antipiracy.fi Copyright Information & Anti-Piracy Centre In Finland | And We'll keep it down as long as We want \o/," tweeted @anon_finland.
"To re-iterate: F-Secure supports the censorship in Finland and #elisagate. Boycott f-secure warez asap!" tweeted the AnonymouSabu account. At the time of writing the ifpi.fi site was still down.
Wednesday, January 11, 2012
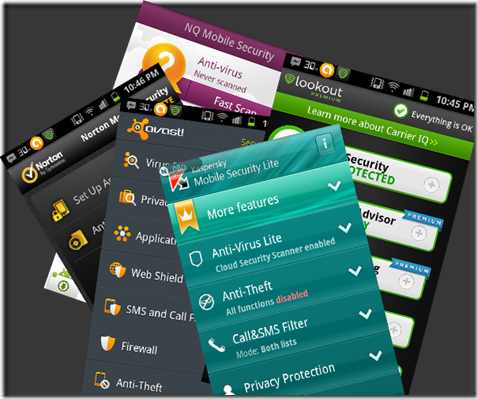
Your Android really needs Antivirus Security ?
Why shouldn't you protect your Android phone? Why to use an Antivirus for your Android? So that users can protect their devices from trojans, viruses, spyware, and other types of malware. Most people carry a lot of sensitive data on their phones. Recently an SMS Trojan horse posing as a media player began infecting Android phones on Russian networks. Once the victim installed the malicious app, it began sending text messages to premium numbers, leaving the user with a huge phone bill.
Labels:
Downloads,
Hacking News,
Security News,
Software,
Virus
Subscribe to:
Posts (Atom)